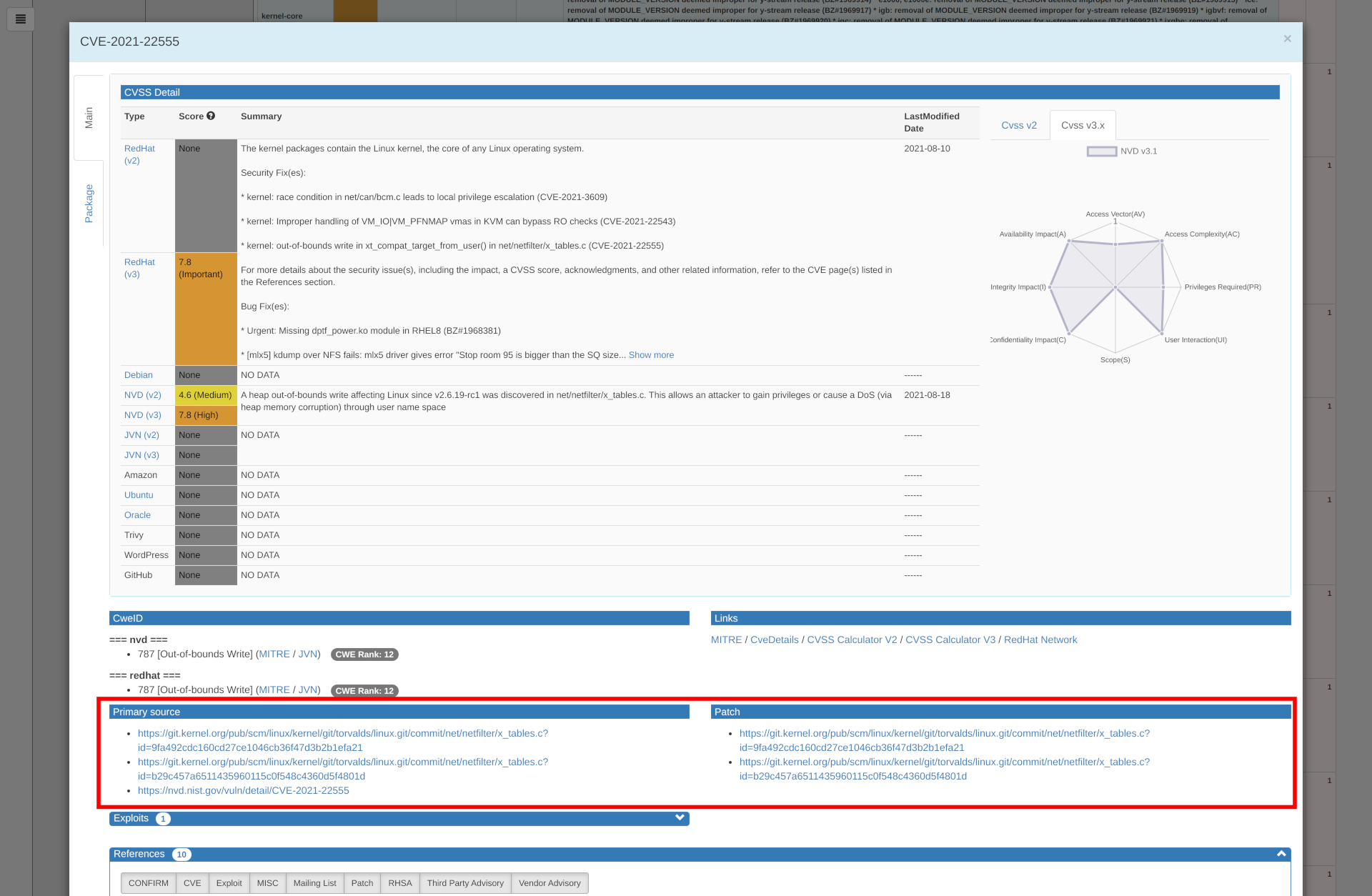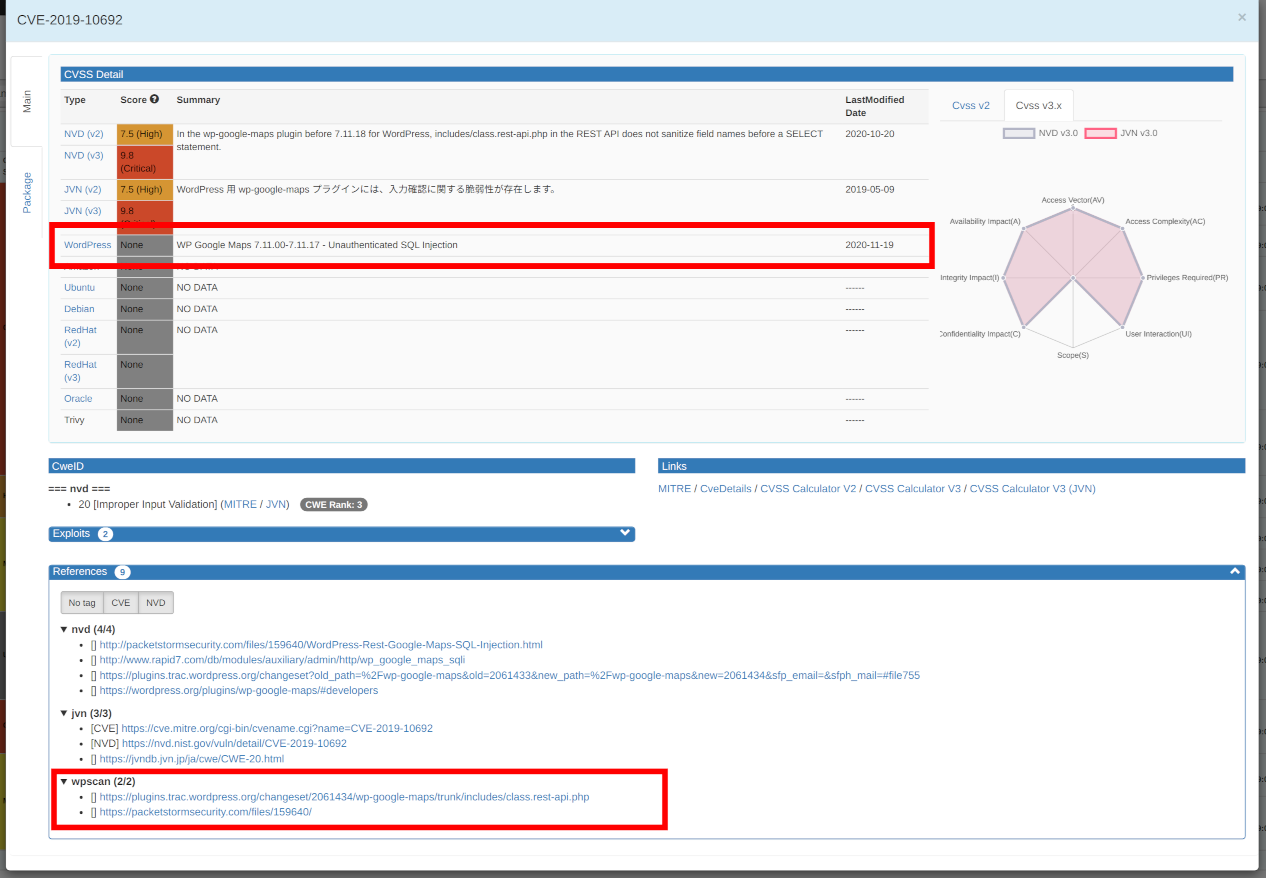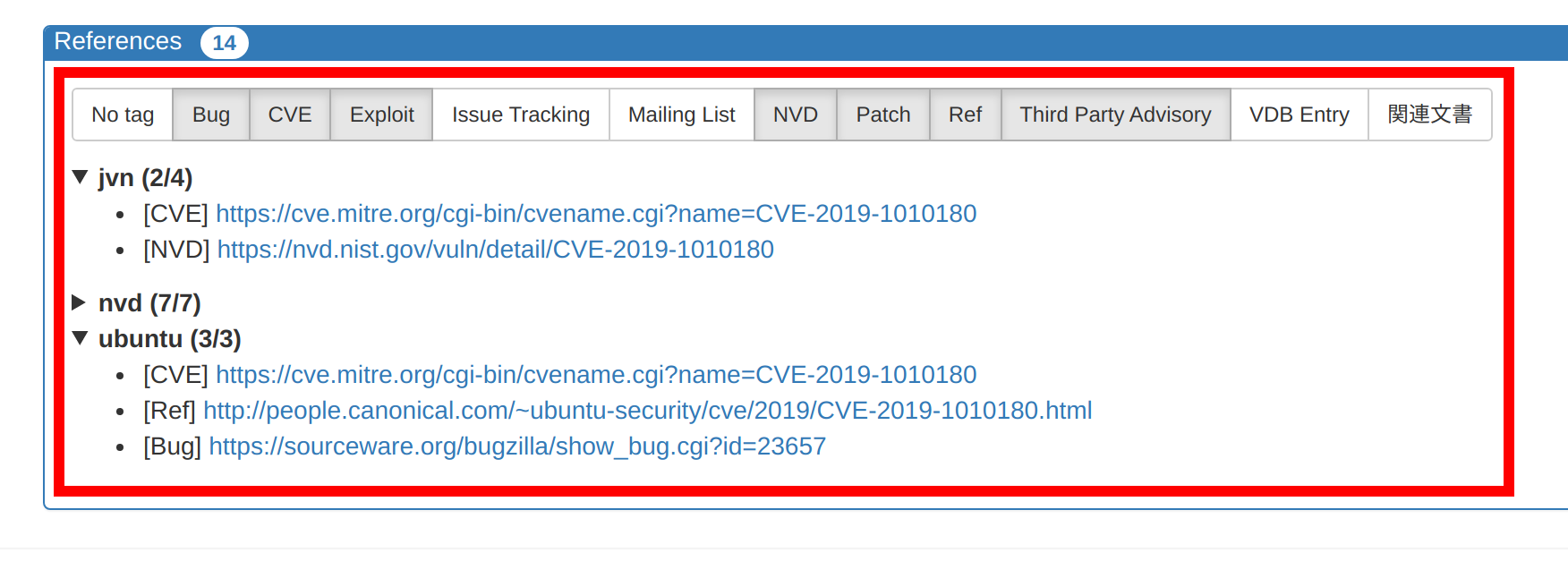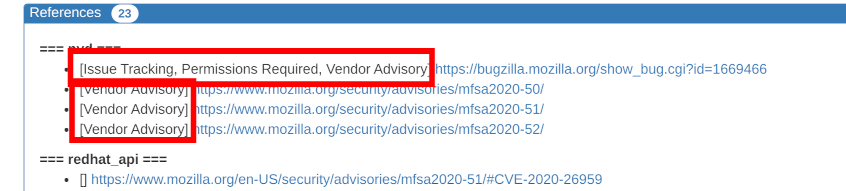
With this update, if you have a predetermined server, time period, and filter, you can specify the various parameters in the URL when you open VulsRepo, saving you the trouble of manually selecting them each time.
Previously, you had to open VulsRepo, manually select the date and server, press the Submit button, and then select the filter if necessary.
Features
- #189 It is now possible to select the data to be displayed by specifying several parameters.
The following parameters can be specified.
| Parameter | Purpose | Value |
|---|---|---|
| server | Target server (container) | For all, all. If more than one, concatenate them with +. ex)foo.json, foo.json+bar.json+baz@foo.json |
| daterange | Date Range | today, yesterday, last7days, last30days, thismonth, lastmonth or alldays |
| datefrom | Date Range from (*) | YYYY-MM-DD format ex)2020-11-01 |
| dateto | Date Range to (*) | YYYY-MM-DD format ex)2021-01-23 |
| time | Specific date and time | ISO8601 format ex) 2020-02-04T01:25:11Z or 2021-01-25T12:34:56+09:00 |
| filter | Specifying a filter | Filter name. If not specified, no filter ex) 01.%20Graph:%20CVSS-Severity%20=>%20ServerName |
(*) datefrom and dateto must be specified as a set.
Priority of date-related parameters
High daterange > datefrom and dateto > time Low
If none of these are specified, the latest date will be set.
Examples
Here are some examples.
localhost.json of the latest date
https://monocosel.jp/vulsrepo/?server=localhost.json
localhost.json and raspberry10.json for the last 30 days
https://monocosel.jp/vulsrepo/?daterange=last30days&server=localhost.json+raspberry10.json
All servers (containers) from 2020-09-18 to 2020-11-16
https://monocosel.jp/vulsrepo/?datefrom=2020-09-18&dateto=2020-11-16&server=all
localhost.json on 2020-02-04T01:25:11Z
https://monocosel.jp/vulsrepo/?time=2020-02-04T01:25:11Z&server=localhost.json
localhost.json and vulsrepo@localhost.json on 2020-02-04T01:25:11Z
localhost.json on 2020-02-04T01:25:11Z with 01. Graph: CVSS-Severity => ServerName filter
localhost.json on 2020-02-04T01:25:11Z with 02. Graph: CVSS-Severity => CVSS-Score filter
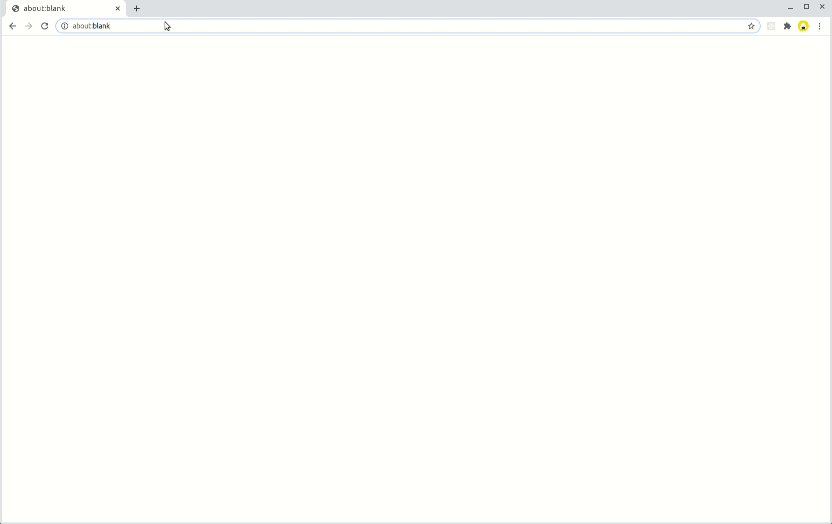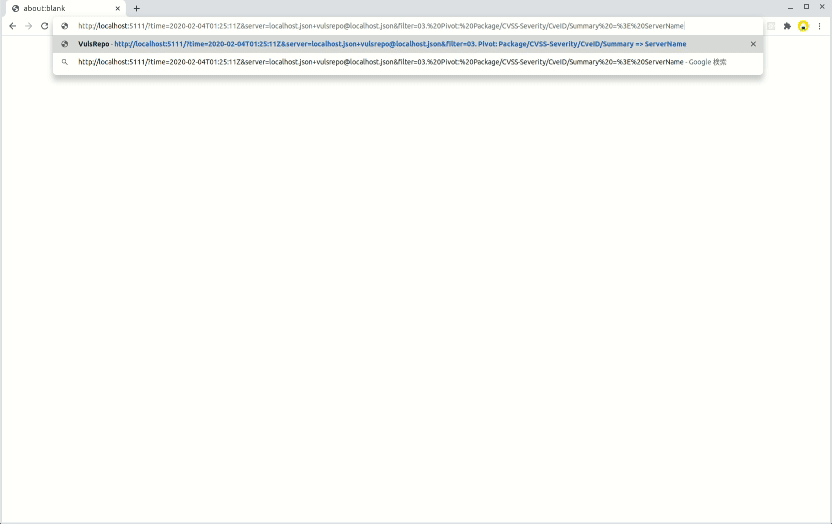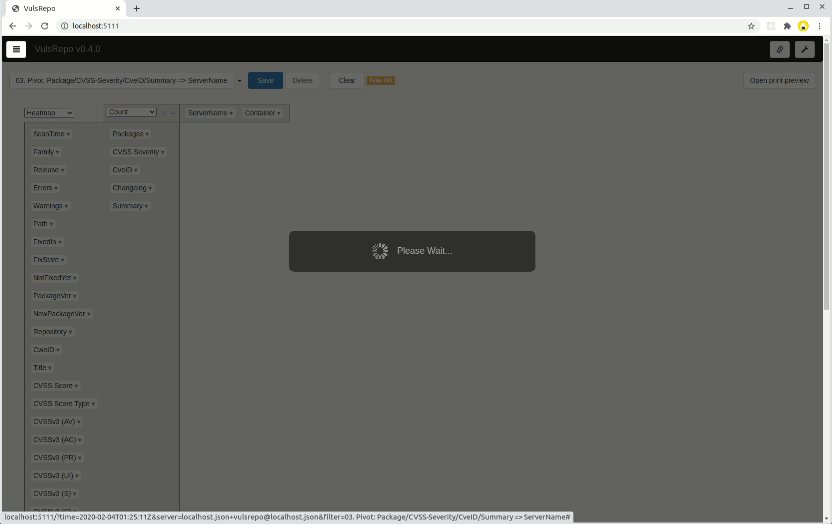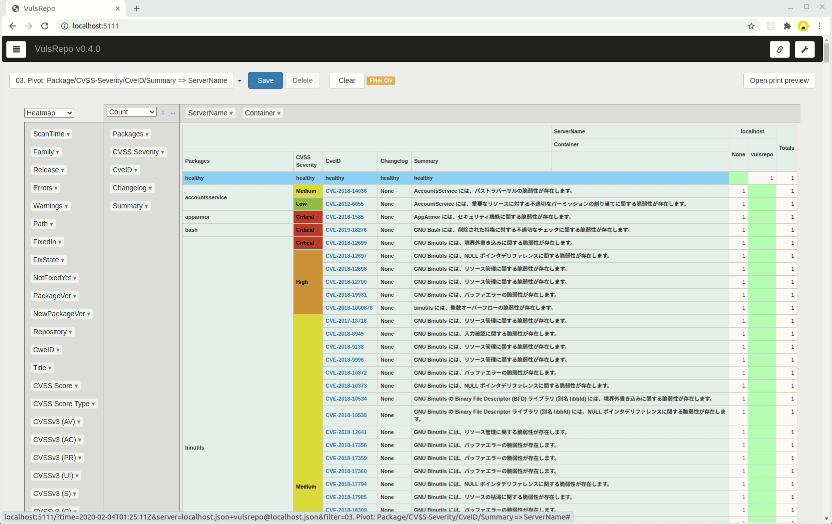
localhost.json on 2020-02-04T01:25:11Z with 03. Pivot: Package/CVSS-Severity/CveID/Summary => ServerName filter
localhost.json on 2020-02-04T01:25:11Z with 04. Pivot: Package/CveID => ScanTime filter
localhost.json on 2020-02-04T01:25:11Z with 05. Pivot: CveID/PackageInfo => NotFixedYet filter
Changes
- Nothing.
Fixes
- #189 Removed debug log.
Docker image
ishidaco/vulsrepo - Docker Hub
docker pull ishidaco/vulsrepo
docker pull ishidaco/vulsrepo:version-0.4.0
Demo
VulsRepo online demo is here.
You can see a sample of the following vulnerability scan results.
- Amazon Linux 2
- Ubuntu 18.04
- Raspbian 9.13
- Raspberry Pi OS 10
- Oracle Linux 7.9
- CentOS 8.2
- Debian 10
- Alpine Linux on Docker container
- Ubuntu 14.04 on Docker container
See also https://github.com/ishiDACo/vulsrepo/releases/tag/v0.4.0